| |||
next generation firewalla next generation firewall (ngfw). thumbnails are cropped (where applicable), scaled-down versions of the original image. to see the un-cropped, full-size original image, which will open in a new window, click its respective thumbnail. for far too long, both television shows and theatrical movies have given far too much credit to the stupidest of stupidest network security devices, the firewall. access through a firewall is dependant upon an access control list (acl). this can be some combination of mac address, ip address, port, protocol, subnet, etc. any assumed "unique" qualifier in an acl can easily be spoofed. essentially, a firewall is a door with a key lock without care of the holder of the key, just that there's a key. if a firewall is a door with a key lock, a next generation firewall is a door with a key lock, pin pad, rfid/magnetic card reader, and a secret knock (with a camera). in essence, what was once science fiction is now science non-fiction. it's not uncommon to now find things such as intrusion prevention and malware protection built into a firewall. a firewall having such characteristics is categorized as being a next generation firewall (ngfw) this sounds a lot like unified threat management (utm) in a firewall, true. however, utm firewall solutions are heavy, as they should be, on threats whereas the ngfw will often do all that which the utm firewall will do, and more. more as in traffic shaping, qos, load balancing, with the ability to both identify and block traffic based upon application protocol. it's most obvious to see the attractiveness of a ngfw. it's like an exotic sports coupe compared to the domestic family sedan. no surprise, the pricing model for an ordinary firewall to that of a utm firewall or ngfw is like that of the aforementioned car analogy. since i'm a hacker, with an extensive background in information security, i'll roll my own. to accomplish my goal of a do-it-yourself ngfw i'm using what was once a resilience ndurant express 06, sans any of the preloaded resilience or check point software. instead, i plan to use a combination of open source software solutions, such as snort (like way obvi), in conjunction with writing my own software solutions when/where necessary. what will be my ngfw is currently configured with:
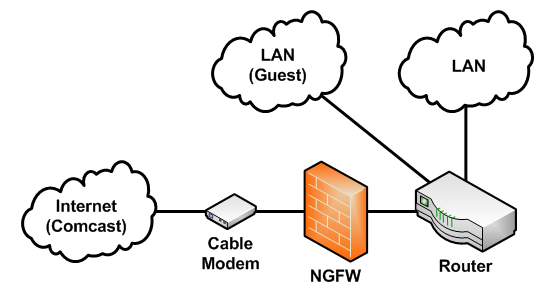
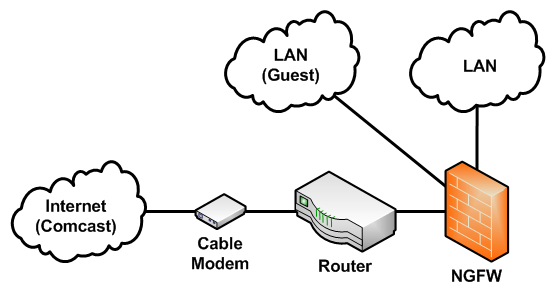
there's an unused pata port which can be utilized to support more secondary storage, such as at least one additional compactflash card or pata drive (or both). placement of the ngfw in the network (my home network) will either be in front of or behind of the edge router. both placements have their advantages and disadvantages.
having the ngfw in front of the edge router will increase the amount of undesired traffic processed by the ngfw. strain on the edge router will be less than it is now. this allows for both lan segments to be processed jointly which will require one acl. for me, both less work and cabling as well as more trusted devices. not to mention, "ocd unfriendly".
having the ngfw behind of the edge router will decrease the amount of undesired traffic processed by the ngfw. strain on the edge router will be no different than it is now given no ngfw exists in the network today. this also allows for better processing of traffic as both network lan segments can be handled independently, but will require two separate acls. for me, both more work and cabling as well as fewer trusted devices. while "ocd friendly", it leaves the edge router exposed. | |||
|
©mmxvii ickis, ickis@nerpter77.com |