| |||||||
rantings & ravings (october 2022)these are opinions, the only ones that matter (to me, mine), on both various stuffs and various things.
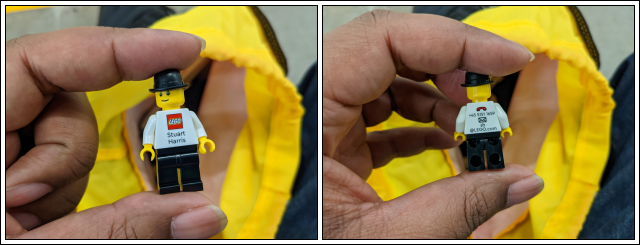
brickcon_2022 brickcon 2022saturday, october 1st (international day of coffee; international day of older persons) typically, i don't write about brickcon... 'cause... i just don't? this was my fifth one, fourth in-person. [shakes a fist at 2020.] i've been to the last five. anyway, this one was really cool for two things.... i missed stuart harris' presentation about the lego house. i think i was in a parts draft, i just recall there was a conflict and a parts draft would win out over anything else (at least they have so far). i'm fairly certain stuart has given this presentation at a prior brickcon, and that i saw it at least in part, but i don't think he was in-person giving it. a co-worker that i hang out with at the con mentioned how he got stuart's business card and shows me this minifigure. so, i had to have one too... obvi. i forget what day of the con this was too.
anyway, just a chance thing on the last day of the con, as everything is over and done with save for tearing down and packing up and leaving, i see stuart who seems poised to be leaving the convention hall. i ask him if i could have his business card and huzzah! he gives me one!
i asked him about the "wash your hands" image i saw being passed around earlier during this pandemic. i knew the first image i saw used his business card minifig, but i didn't know it was truly him who took and posted the photo to instagram. i had made my own to mock the copycats that were making the rounds at the time. he also spied the book i had with me, building a dream (more on that later). he tells me it's a good read or something to that effect. he also mentions how page 92 is the best. i keep this in mind.
prior to talking to stuart, during the con's closing ceremonies, i won something... finally! no, not a lego set, which i would have wanted. but no, no door prize for me. however, i did get selected for a "chance to win" prize thing, for making a charity donation, which happened to be a book, building a dream. you may have heard about it before. you could have gotten a copy from the lego house in denmark (and maybe still can, it's a limited printing it has been reported)... or still can get one from ebay probably. oh... but mine is also signed by kjeld kirk kristiansen, the grandson of ole kirk kristiansen, founder of lego. so... there's that. i didn't know i wanted this book until i won it. also, page 92... it's a picture of stuart. well played stuart, well played. mfa_2fa_what_are_they mfa, 2fa, what are they?saturday, october 1st (international day of coffee; international day of older persons) since it's cybersecurity month and all... i've adapted this from something i wrote for work, stripping out references to my employer: When you attempt to access a secured system, whether that be a digital system, like a computer, or a physical system, like a facility, you need to provide a factor. A factor can be thought of as a password, like for a computer, or a keycard, like for a facility. However, passwords can be surreptitiously obtained or even stolen, and keys can be lost or stolen as well. To combat against this, an additional factor can be combined with the first. This is known as MFA, more specifically, 2FA. MFA is multi-factor authentication and 2FA is two-factor authentication. In the same way that all squares are rectangles, but not all rectangles are squares, 2FA is MFA, but not all MFA is 2FA. While one term is a subset of the other, many people use these terms interchangeably. | |||||||
|
©mmxxii ickis, ickis@nerpter77.com |